Generate A Private Key Java Keytool
Related
- Generate Private Key Using Keytool
- Java Keytool Private Key
- Private Key Bitcoin
- Generate A Private Key Java Keytool Download
In this tutorial, we demonstrate how to extract a private key from the Java KeyStore (JKS) in your projects using OpenSSL and Keytool. Extracting a Private Key From the Java Keystore (JKS) - DZone. Topic - (1) Using keytool to generate a public-private key pair. The first step in configuring a VT Display session for SSH client authentication using a public key is to use the keytool program to generate a public-private key pair. About keytool. Keytool is a multipurpose utility program, included in the Java 2 Version 1.4 JRE and distributed with Host On-Demand, for managing keys. To Use keytool to Create a Server Certificate. Run keytool to generate a new key pair in the default development keystore file, keystore.jks.This example uses the alias server-alias to generate a new public/private key pair and wrap the public key into a self-signed certificate inside keystore.jks. Apr 23, 2012 RSA authentication uses public and private keys instead of passwords to authenticate with the ESP Server. The Java keytool utility is used to generate RSA keys when the client is in Java. Open a command prompt or terminal. Private Key import. Keytool 은 외부에서 생성된 private key 를 keystore 에 import 하는 방법을 제공하지 않는다. 한 가지 방법은 JDK 6 이상부터 PKCS#12 으로 된 인증서와 개인키를 keystore 에 import 하는게 가능하므로 openssl 로 pkcs#12 를 만들고 pkcs#12 를 KeyStore 로임포트하면 된다. Jan 25, 2018 Java keytool genkey FAQ: Can you share some examples of the Java keytool genkey command, and the genkey process? In my previous article on the Java keytool command, keystore files, and certificates, I demonstrated how to generate a private key with the keytool genkey option, but to simplify things a little, I thought I'd demonstrate the keytool/genkey command again here by itself.
Introduction
Java Keytool is a key and certificate management tool that is used to manipulate Java Keystores, and is included with Java. A Java Keystore is a container for authorization certificates or public key certificates, and is often used by Java-based applications for encryption, authentication, and serving over HTTPS. Its entries are protected by a keystore password. A keystore entry is identified by an alias, and it consists of keys and certificates that form a trust chain.
This cheat sheet-style guide provides a quick reference to keytool commands that are commonly useful when working with Java Keystores. This includes creating and modifying Java Keystores so they can be used with your Java applications.
How to Use This Guide:
- If you are not familiar with certificate signing requests (CSRs), read the CSR section of our OpenSSL cheat sheet
- This guide is in a simple, cheat sheet format–self-contained command line snippets
- Jump to any section that is relevant to the task you are trying to complete (Hint: use the Contents menu on the bottom-left or your browser’s Find function)
- Most of the commands are one-liners that have been expanded to multiple lines (using the
symbol) for clarity
Creating and Importing Keystore Entries
This section covers Java Keytool commands that are related to generating key pairs and certificates, and importing certificates.
Generate Keys in New/Existing Keystore
Use this method if you want to use HTTP (HTTP over TLS) to secure your Java application. This will create a new key pair in a new or existing Java Keystore, which can be used to create a CSR, and obtain an SSL certificate from a Certificate Authority.
This command generates a 2048-bit RSA key pair, under the specified alias (domain), in the specified keystore file (keystore.jks):
If the specified keystore does not already exist, it will be created after the requested information is supplied. This will prompt for the keystore password (new or existing), followed by a Distinguished Name prompt (for the private key), then the desired private key password.
Generate CSR For Existing Private Key
Use this method if you want to generate an CSR that you can send to a CA to request the issuance of a CA-signed SSL certificate. It requires that the keystore and alias already exist; you can use the previous command to ensure this.
This command creates a CSR (domain.csr) signed by the private key identified by the alias (domain) in the (keystore.jks) keystore:
After entering the keystore’s password, the CSR will be generated.
Import Signed/Root/Intermediate Certificate
Use this method if you want to import a signed certificate, e.g. a certificate signed by a CA, into your keystore; it must match the private key that exists in the specified alias. You may also use this same command to import root or intermediate certificates that your CA may require to complete a chain of trust. Simply specify a unique alias, such as root instead of domain, and the certificate that you want to import.
This command imports the certificate (domain.crt) into the keystore (keystore.jks), under the specified alias (domain). If you are importing a signed certificate, it must correspond to the private key in the specified alias:
You will be prompted for the keystore password, then for a confirmation of the import action.
Note: You may also use the command to import a CA’s certificates into your Java truststore, which is typically located in $JAVA_HOME/jre/lib/security/cacerts assuming $JAVA_HOME is where your JRE or JDK is installed.
Generate Self-Signed Certificate in New/Existing Keystore
Use this command if you want to generate a self-signed certificate for your Java applications. This is actually the same command that is used to create a new key pair, but with the validity lifetime specified in days.
This command generates a 2048-bit RSA key pair, valid for 365 days, under the specified alias (domain), in the specified keystore file (keystore.jks):
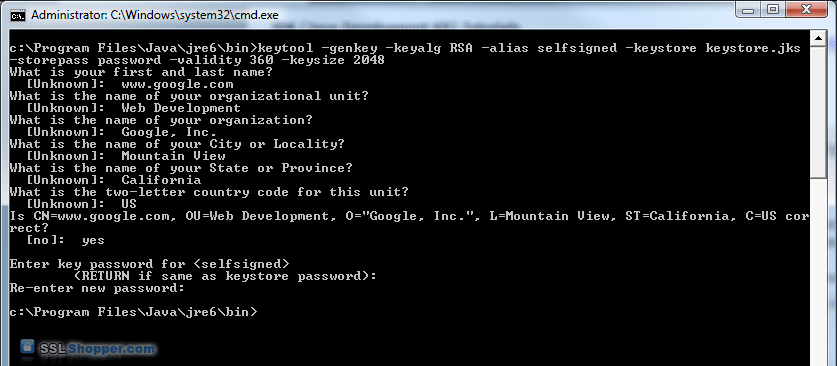
If the specified keystore does not already exist, it will be created after the requested information is supplied. This will prompt for the keystore password (new or existing), followed by a Distinguished Name prompt (for the private key), then the desired private key password.
Generate Private Key Using Keytool
Viewing Keystore Entries
This section covers listing the contents of a Java Keystore, such as viewing certificate information or exporting certificates.
List Keystore Certificate Fingerprints
This command lists the SHA fingerprints of all of the certificates in the keystore (keystore.jks), under their respective aliases:
You will be prompted for the keystore’s password. You may also restrict the output to a specific alias by using the -alias domain option, where “domain” is the alias name.
List Verbose Keystore Contents
This command lists verbose information about the entries a keystore (keystore.jks) contains, including certificate chain length, fingerprint of certificates in the chain, distinguished names, serial number, and creation/expiration date, under their respective aliases:
You will be prompted for the keystore’s password. You may also restrict the output to a specific alias by using the -alias domain option, where “domain” is the alias name.
Note: You may also use this command to view which certificates are in your Java truststore, which is typically located in $JAVA_HOME/jre/lib/security/cacerts assuming $JAVA_HOME is where your JRE or JDK is installed.
Use Keytool to View Certificate Information
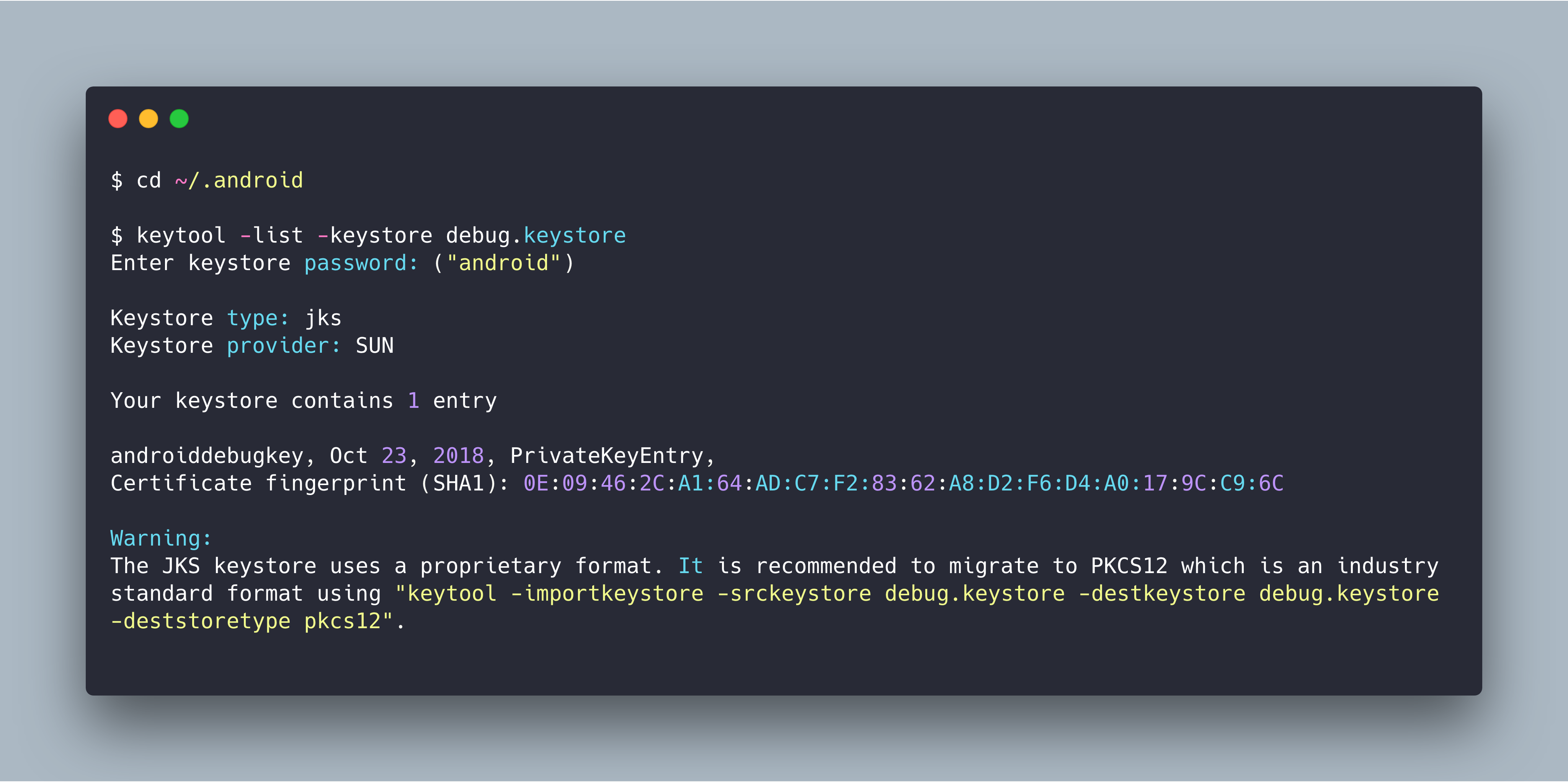
Java Keytool Private Key
This command prints verbose information about a certificate file (certificate.crt), including its fingerprints, distinguished name of owner and issuer, and the time period of its validity:
You will be prompted for the keystore password.
Export Certificate
This command exports a binary DER-encoded certificate (domain.der), that is associated with the alias (domain), in the keystore (keystore.jks):
You will be prompted for the keystore password. If you want to convert the DER-encoded certificate to PEM-encoding, follow our OpenSSL cheat sheet.
Modifying Keystore
This section covers the modification of Java Keystore entries, such as deleting or renaming aliases.
Change Keystore Password
This command is used to change the password of a keystore (keystore.jks):
You will be prompted for the current password, then the new password. You may also specify the new password in the command by using the -new newpass option, where “newpass” is the password.
Delete Alias
This command is used to delete an alias (domain) in a keystore (keystore.jks):
You will be prompted for the keystore password.
Rename Alias
This command will rename the alias (domain) to the destination alias (newdomain) in the keystore (keystore.jks):
You will be prompted for the keystore password.
Conclusion
That should cover how most people use Java Keytool to manipulate their Java Keystores. It has many other uses that were not covered here, so feel free to ask or suggest other uses in the comments.
This tutorial is based on the version of keystore that ships with Java 1.7.0 update 65. For help installing Java on Ubuntu, follow this guide.
If a code signer does not yet have a suitable private key for signing the code, the key must first be generated, along with a corresponding public key that can be used by the code receiver's runtime system to verify the signature.
Since this lesson assumes that you don't yet have such keys, you are going to create a keystore named examplestore and create an entry with a newly generated public/private key pair (with the public key in a certificate).
Type the following command in your command window to create a keystore named examplestore and to generate keys:
You will be prompted to enter passwords for the key and keystore.
Subparts of the keytool Command
Let's look at what each of the keytool subparts mean.
- The command for generating keys is -genkey.
- The -alias signFiles subpart indicates the alias to be used in the future to refer to the keystore entry containing the keys that will be generated.
- The -keystore examplestore subpart indicates the name (and optionally path) of the keystore you are creating or already using.
- The storepass value that you are promted for specifies the keystore password.
- The keypass value that you are prompted for specifies a password for the private key about to be generated. You will always need this password in order to access the keystore entry containing that key. The entry doesn't have to have its own password. When you are prompted for the key password, you are given the option of letting it be the same as the keystore password.
Note: For security reasons you should not set your key or keystore passwords on the command line, because they can be intercepted more easily that way.
Distinguished-Name Information
If you use the preceding keystore command, you will be prompted for your distinguished-name information. /aws-ec2-generate-key-pair-sshgen.html. Following are the prompts; the bold indicates what you should type.
Command Results
Private Key Bitcoin
The keytool command creates the keystore named examplestore (if it doesn't already exist) in the same directory in which the command is executed. The command generates a public/private key pair for the entity whose distinguished name has a common name of Susan Jones and the organizational unit of Purchasing.
The command creates a self-signed certificate that includes the public key and the distinguished-name information. (The distinguished name you supply will be used as the 'subject' field in the certificate.) This certificate will be valid for 90 days, the default validity period if you don't specify a -validity option. The certificate is associated with the private key in a keystore entry referred to by the alias signFiles.
Self-signed certificates are useful for developing and testing an application. However, users are warned that the application is signed with an untrusted certificate and asked if they want to run the application. To provide users with more confidence to run your application, use a certificate issued by a recognized certificate authority.
Generate A Private Key Java Keytool Download
Note: The command could be shorter if option defaults are accepted or you wish to be prompted for various values. Whenever you execute a keytool command, defaults are used for unspecified options that have default values, and you are prompted for any required values. For the genkey command, options with default values include alias (whose default is mykey), validity (90 days), and keystore (the file named .keystore in your home directory). Required values include dname, storepass, and keypass.